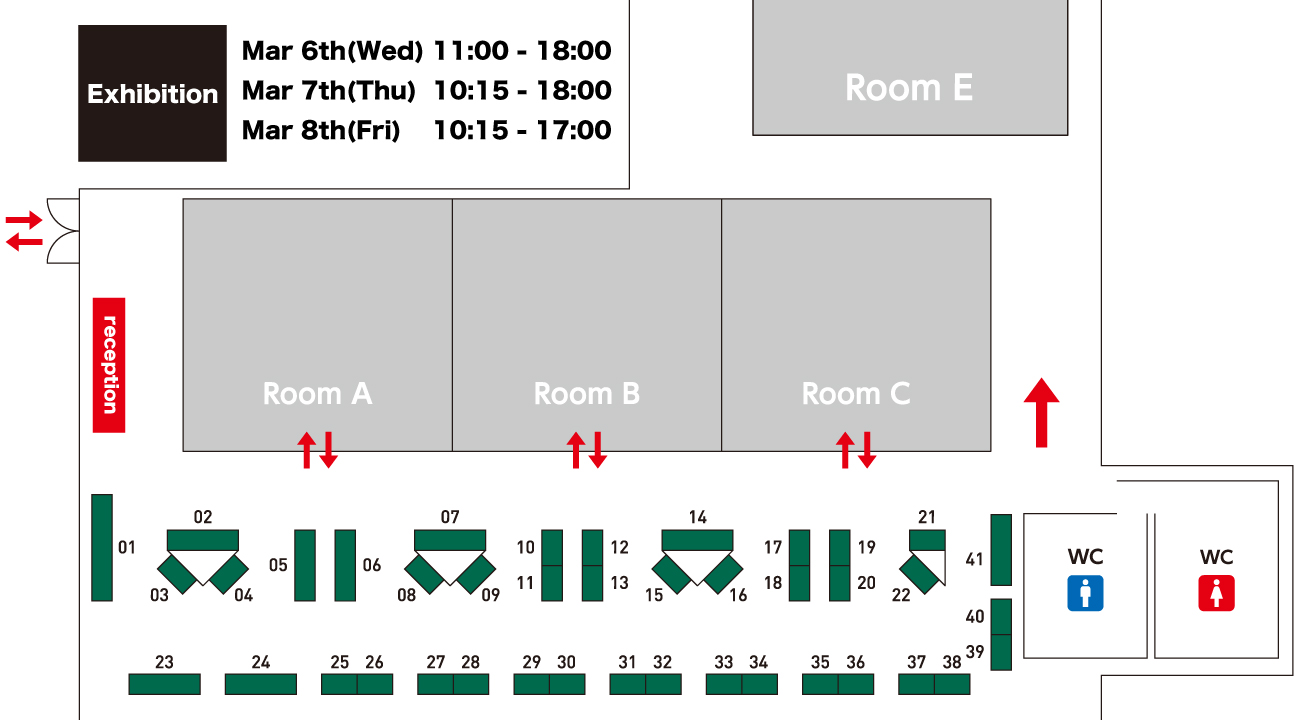
Exhibition
KEYWORDS
Targeted Theat
Email Security
Ransomware measures
Firewall / UTM
Antivirus
Endpoint Security
Domain authentication / DNS security
Measures against information leakage
Authentication / Identity Management
Measures against DDoS
Remote access / VPN
IoT security
Vulnerability countermeasure / Tamper prevention measures
Incident response / CSIRT / SOC
Cloud security
Critical Infrastructure Security
GDPR / Privacy Mark / ISMS / Trends of laws and ordinances
Smart device security
Monitoring and detection
AI
Human resource development
Security auditing / System audit
Business Email Compromise (BEC) countermeasures
Phishing Attack
Work style reforms
Improve productivity
Other
ALL
Booth
- 37Ad-Sol Nissin
- 17Akamai Technologies
- 01Antuit
- 36AP Communications
- 39ASK
- 13Brainzsquare
- 14Canon Marketing Japan
- 30Computer Futures
- 12Cybereason Japan
- 32CYBERGYM TOKYO
- 03Darktrace
- 06Encourage Technologies
- 31FFRI
- 11FireEye
- 20F-Secure
- 02/04HAMMOCK
- 24Hitachi Solutions
- 40Infoblox
- 38KOZO KEIKAKU ENGINEERING
- 16Lookout
- 07/08NEC Solution Innovators / Cylance Japan
- 27Netskope Japan
- 19Network Value Components
- 29NTT Communications
- 09NTT TechnoCross
- 05OPSWAT JAPAN / Net One Partners
- 18Optima Solutions
- 35ORIZON Systems
- 23PIOLINK
- 33Portwell Japan
- 15Proofpoint / TechMatrix
- 25RSA
- 34SANS Institute
- 21/22SecureWorks Japan
- 10Soliton Systems
- 28Symantec
- 26TERILOGY WORX
- 41WatchGuard Technologies
Ad-Sol Nissin
Platinum Sponsor
KEYWORD
- Measures against DDoS
- IoT security
- Critical Infrastructure Security
CONTACT
| TEL | |
|---|---|
| FAX | |
| URL |
Akamai Technologies
Gold Sponsor
KEYWORD
- Targeted Theat
- Remote access / VPN
- Vulnerability countermeasure / Tamper prevention measures
CONTACT
| TEL | |
|---|---|
| URL |
Antuit
Platinum Sponsor
KEYWORD
- Targeted Theat
- Incident response / CSIRT / SOC
- AI
CONTACT
| TEL | |
|---|---|
| FAX | |
| URL |
AP Communications
Bronze Sponsor
KEYWORD
- Firewall / UTM
- Work style reforms
- Improve productivity
CONTACT
| TEL | |
|---|---|
| FAX | |
| URL |
ASK
Bronze Sponsor
KEYWORD
- IoT security
- Critical Infrastructure Security
CONTACT
| TEL | |
|---|---|
| FAX | |
| URL |
Brainzsquare
Silver Sponsor
KEYWORD
- Measures against information leakage
- Ransomware measures
- Endpoint Security
CONTACT
| TEL | |
|---|---|
| FAX | |
| URL |
Canon Marketing Japan
Platinum Sponsor
KEYWORD
- Targeted Theat
- Antivirus
- Endpoint Security
CONTACT
| URL |
|---|
Computer Futures
Bronze Sponsor
KEYWORD
- Other
CONTACT
| TEL | |
|---|---|
| FAX | |
| URL |
Cybereason Japan
Gold Sponsor
KEYWORD
- Targeted Theat
- Ransomware measures
- Endpoint Security
CONTACT
| URL |
|---|
CYBERGYM TOKYO
Bronze Sponsor
KEYWORD
- Measures against information leakage
- IoT security
- Human resource development
CONTACT
| TEL | |
|---|---|
| FAX | |
| URL |
Darktrace
Bronze Sponsor
KEYWORD
- Monitoring and detection
- AI
CONTACT
| TEL | |
|---|---|
| URL |
Encourage Technologies
Bronze Sponsor
KEYWORD
- Targeted Theat
- Measures against information leakage
- Authentication / Identity Management
CONTACT
| TEL | |
|---|---|
| FAX | |
| URL |
FFRI
Bronze Sponsor
KEYWORD
- Targeted Theat
- Ransomware measures
- Endpoint Security
CONTACT
| TEL | |
|---|---|
| URL |
FireEye
Silver Sponsor
KEYWORD
- Endpoint Security
- Measures against information leakage
- Incident response / CSIRT / SOC
F-Secure
Bronze Sponsor
KEYWORD
- Targeted Theat
- Endpoint Security
- Vulnerability countermeasure / Tamper prevention measures
CONTACT
| TEL | |
|---|---|
| URL |
HAMMOCK
Gold Sponsor
KEYWORD
- Targeted Theat
- Measures against information leakage
- Vulnerability countermeasure / Tamper prevention measures
CONTACT
| TEL | |
|---|---|
| FAX | |
| URL |
Hitachi Solutions
シルバ-スポンサー
KEYWORD
- Endpoint Security
- Authentication / Identity Management
- Cloud security
CONTACT
| TEL | |
|---|---|
| FAX | |
| URL |
Infoblox
Silver Sponsor
KEYWORD
- Domain authentication / DNS security
- Cloud security
- Incident response / CSIRT / SOC
CONTACT
| TEL | |
|---|---|
| URL |
KOZO KEIKAKU ENGINEERING
Bronze Sponsor
KEYWORD
- Targeted Theat
- Incident response / CSIRT / SOC
- Monitoring and detection
CONTACT
| TEL | |
|---|---|
| FAX | |
| URL |
Lookout
Bronze Sponsor
KEYWORD
- Endpoint Security
- Smart device security
- Phishing Attack
CONTACT
| TEL | |
|---|---|
| FAX | |
| URL |
NEC Solution Innovators / Cylance Japan
Silver Sponsor

KEYWORD
- Endpoint Security
- Incident response / CSIRT / SOC
- Work style reforms
Netskope Japan

KEYWORD
- Cloud security
- Monitoring and detection
- Measures against information leakage
CONTACT
| TEL | |
|---|---|
| japan@netskope.com | |
| URL |
Network Value Components

KEYWORD
- Targeted Theat
- Endpoint Security
- Incident response / CSIRT / SOC
CONTACT
| TEL | |
|---|---|
| FAX | |
| URL |
NTT Communications
Bronze Sponsor
KEYWORD
- Endpoint Security
- Incident response / CSIRT / SOC
- Monitoring and detection
NTT TechnoCross
Bronze Sponsor
KEYWORD
- Cloud security
- Monitoring and detection
- Security auditing / System audit
CONTACT
| URL |
|---|
OPSWAT JAPAN / Net One Partners
Gold Sponsor

KEYWORD
- Critical Infrastructure Security
- Cloud security
- Antivirus
CONTACT
| URL |
|---|
Optima Solutions
Bronze Sponsor
KEYWORD
- Cloud security
- GDPR / Privacy Mark / ISMS / Trends of laws and ordinances
- Work style reforms
CONTACT
| TEL | |
|---|---|
| FAX | |
| URL |
ORIZON Systems
Bronze Sponsor
KEYWORD
- Targeted Theat
- Measures against DDoS
- Work style reforms
CONTACT
| TEL | |
|---|---|
| FAX | |
| URL |
PIOLINK
Silver Sponsor
KEYWORD
- Ransomware measures
- IoT security
- Security auditing / System audit
CONTACT
| TEL | |
|---|---|
| FAX | |
| URL |
Portwell Japan
Bronze Sponsor
KEYWORD
- Antivirus
- Endpoint Security
- IoT security
CONTACT
| TEL | |
|---|---|
| FAX | |
| URL |
Proofpoint / TechMatrix
Bronze Sponsor

KEYWORD
- Targeted Theat
- Email Security
- Business Email Compromise (BEC) countermeasures
RSA
Bronze Sponsor
KEYWORD
- Incident response / CSIRT / SOC
- Critical Infrastructure Security
- Improve productivity
CONTACT
| TEL | |
|---|---|
| FAX | |
| URL |
SANS Institute
Silver Sponsor
KEYWORD
- Human resource development
CONTACT
| TEL | |
|---|---|
| URL |
SecureWorks Japan
Gold Sponsor
KEYWORD
- Targeted Theat
- Incident response / CSIRT / SOC
- Monitoring and detection
CONTACT
| TEL | |
|---|---|
| URL |
Soliton Systems
Platinum Sponsor
KEYWORD
- Measures against information leakage
- Authentication / Identity Management
- IoT security
CONTACT
| TEL | |
|---|---|
| 03-5360-3880 | |
| URL |
Symantec
Gold Sponsor
KEYWORD
- Cloud security
- Work style reforms
- Improve productivity
CONTACT
| TEL | |
|---|---|
| FAX | |
| URL |
TERILOGY WORX
Bronze Sponsor
KEYWORD
- Targeted Theat
- Incident response / CSIRT / SOC
- Phishing Attack
CONTACT
| TEL | |
|---|---|
| FAX | |
| URL |
WatchGuard Technologies
Silver Sponsor
KEYWORD
- Targeted Theat
- Business Email Compromise (BEC) countermeasures
- Work style reforms
CONTACT
| TEL | |
|---|---|
| FAX | |
| URL |